UPDATE: This script has been updated to use v2 APIs. Please see the updated version here.
After upgrading my server to a better spec and moving to new data center, I found that the server was getting attacked by botnets trying to brute-force logins and port scanning. Using the ConfigServer Security & Firewall plugin (CSF) on my server I was able to automatically block attackers, but I wanted to go a step further: to report the IPs to the AbuseIPDB.
To achieve this, I wrote a PHP script that can be triggered by by the Login Failure Daemon (LFD) that comes with CSF, which then reports the abusive IPs to AbuseIPDB using their API.
Prerequisites
- CSF / LFD plugin installed and configured
- AbuseIPDB Account
- AbuseIPDB API Key
The PHP Script
I first started by writing a PHP script that could be called from the command line:
The above script captures the arguments sent by LFD in the command line, which includes the remote IP, a message that contains the reason for the IP block and relevant log messages (among other information). The full argument list is as follows:
ARG 1 = IP Address # The IP address or CIDR being blocked
ARG 2 = ports # Port, comma separated list or * for all ports
ARG 3 = permanent # 0=temporary block, 1=permanent block
ARG 4 = inout # Direction of block: in, out or inout
ARG 5 = timeout # If a temporary block, TTL in seconds, otherwise 0
ARG 6 = message # Message containing reason for block
ARG 7 = logs # The logs lines that triggered the block (will contain
# line feeds between each log line)
ARG 8 = trigger # The configuration settings triggered
The script then check if the IP has already been reported by your account (lines 44-60). If the IP hasn’t been reported, a new report is created on AbuseIPDB (line 65). The above script only checks reports from the last 10 days (line 46, days=10).
The verbose flag (line 46) is used in the API to return additional information on each report, including the AbuseIPDB User ID who created the report. This is used to make sure you don’t report the same IP more than once in a 10 day period.
I stored the script in /root/lfd.php and added the relevant execution permissions using chmod 755 lfd.php.
Thanks to line 1 in the above code, you can simply run lfd.php in the command line and it will trigger the PHP code (without the need for the php prefix).
Configuring CSF / LFD
Once the script was ready, I updated the CSF configuration to trigger the script:
- Edit
/etc/csf/csf.confusing your favourite editor - Find the line starting with
BLOCK_REPORT - Update the line so it reads:
BLOCK_REPORT = "/root/lfd.php" - Restart
lfdusingservice lfd restartor using the web interface
Testing
To test the script, you can either trigger the PHP script manually or wait for a block event to occur. To test manually, you can run the following command line:
/root/lfd.php "REMOTE_IP" "PORTS" "1" "*" "*" "blocked REMOTE_IP for SSH brute force" "sshd"
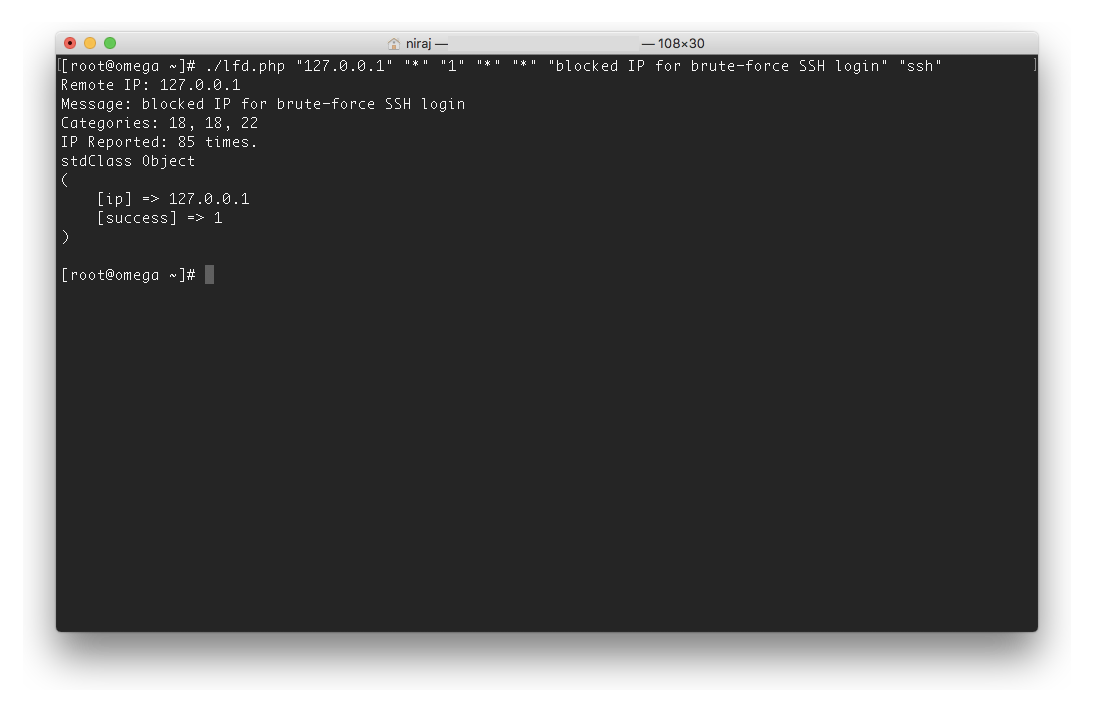
The above command line mimics what LFD would send to the script when a block has occurred. If successful, the command line will display the output of the script, including the IP that was reported:
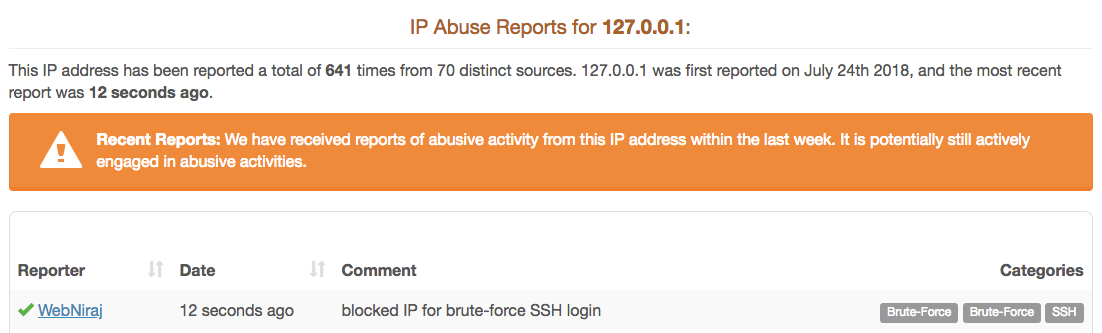
If the AbuseIPDB API reports success in the output, you will be able to see the corresponding report on the website:
As a result of this script running for a few days (and with some manual reporting before the script was setup), I’ve been able to report over a hundred IPs:

Hi. Thank you for this script I’ve been using it for some months now to report to AbuseiP.
Unfortunately, AbuseIP have deprecated APIv1 superceded by APIv2. I have created the new API key for APIv2 and in running it through the lfd.php script, get the problem:
PHP Warning: file_get_contents(https://www.abuseipdb.com/report/json?key=somekey&category=18,22&comment=blocked+REMOTE_IP+for+SSH+brute+force&ip=127.0.0.1): failed to open stream: HTTP request failed! HTTP/1.1 429 Too Many Requests
in /root/lfd.php on line 69
Any ideas what would need changing in the script to make it compatible with APIv2 ?
Thanks.
The error you’re getting suggests that you exceeded your API quota. Wait a while and try again. Check AbuseIPDB to see how much quota you have left too.
Hi Niraj. Thanks for your reply, you were correct. However, please note the response from AbuseIP for a recommendation to change the script slightly:
”
You’re hitting your daily rate limit for checks and reports (1,000 each, for a total of 2,000).
Migrating to APIv2 won’t solve this issue specifically, but to make the script work with APIv2, the “category” parameter should be renamed to “categories” and PHP’s cURL (http://php.net/manual/en/book.curl.php) must be used to report IPs (POST to the endpoint).
”
Your thoughts?
The script could easily be modified to make use of cURL instead of
file_get_contents. When I get some time, I’ll update the code to use the v2 API.I’ve just posted the v2 version of this script.
Thanks for this – bookmarking – I want to give it a try on my server and will report back 🙂
Please add comment when updated to APIv2
I’ve just posted the v2 version of this script.
Awesome of the update for v2. I think a lot of us are going to run into this problem in the coming months.
I’ve just posted the v2 version of this script.
[…] to popular demand, I have upgraded my initial LFD reporting script to use the IP Abuse DB v2 APIs. This post covers the new script and how it can be used. Please read […]
Hello Niraj. Thank you for writing this script.
I have a unique situation with my setup running multiple domains and a lot of my traffic is script kiddies, so I did some modifications (This is V1) and thought I would share with others. The database insert at the end is used by a reporting script I made so that I could determine my most active script kiddies, allowing me to permanently add them to the firewall.
Doug
#!/usr/bin/php
Share a link to your script as it didn’t appear in your post. Also, v2 of the script has been added here.