Due to popular demand, I have upgraded my initial LFD reporting script to use the IP Abuse DB v2 APIs. This post covers the new script and how it can be used. Please read my previous post to understand the background of the script.
Prerequisites
- CSF / LFD plugin installed and configured
- AbuseIPDB Account
- AbuseIPDB APIv2 Key
The PHP Script
The PHP script is designed to be called from the command line. It has been updated to use v2 of the Abuse IP DB API.
The above script captures the arguments sent by LFD in the command line, which includes the remote IP, a message that contains the reason for the IP block and relevant log messages (among other information). The full argument list is as follows:
ARG 1 = IP Address # The IP address or CIDR being blocked
ARG 2 = ports # Port, comma separated list or * for all ports
ARG 3 = permanent # 0=temporary block, 1=permanent block
ARG 4 = inout # Direction of block: in, out or inout
ARG 5 = timeout # If a temporary block, TTL in seconds, otherwise 0
ARG 6 = message # Message containing reason for block
ARG 7 = logs # The logs lines that triggered the block (will contain # line feeds between each log line)
ARG 8 = trigger # The configuration settings triggered
The script then check if the IP has already been reported by your account (lines 87-97). If the IP hasn’t been reported, a new report is created on AbuseIPDB (line 102). The above script only checks reports from the last day (line 88, maxAgeInDays=1).
The verbose flag (line 88) is used in the API to return additional information on each report, including the AbuseIPDB User ID who created the report. This is used to make sure you don’t report the same IP more than once in 24 hour period.
I stored the script in /root/lfd-v2.php and added the relevant execution permissions using chmod 755 lfd-v2.php.
Thanks to line 1 in the above code, you can simply run lfd-v2.php in the command line and it will trigger the PHP code (without the need for the php prefix).
Configuring CSF / LFD
Once the script was ready, I updated the CSF configuration to trigger the script:
- Edit
/etc/csf/csf.confusing your favourite editor - Find the line starting with
BLOCK_REPORT - Update the line so it reads:
BLOCK_REPORT = "/root/lfd-v2.php" - Restart
lfdusingservice lfd restartor using the web interface
Testing
To test the script, you can either trigger the PHP script manually or wait for a block event to occur. To test manually, you can run the following command line:
/root/lfd-v2.php "REMOTE_IP" "PORTS" "1" "*" "*" "blocked REMOTE_IP for SSH brute force" "sshd"
The above command line mimics what LFD would send to the script when a block has occurred. If successful, the command line will display the output of the script, including the IP that was reported:
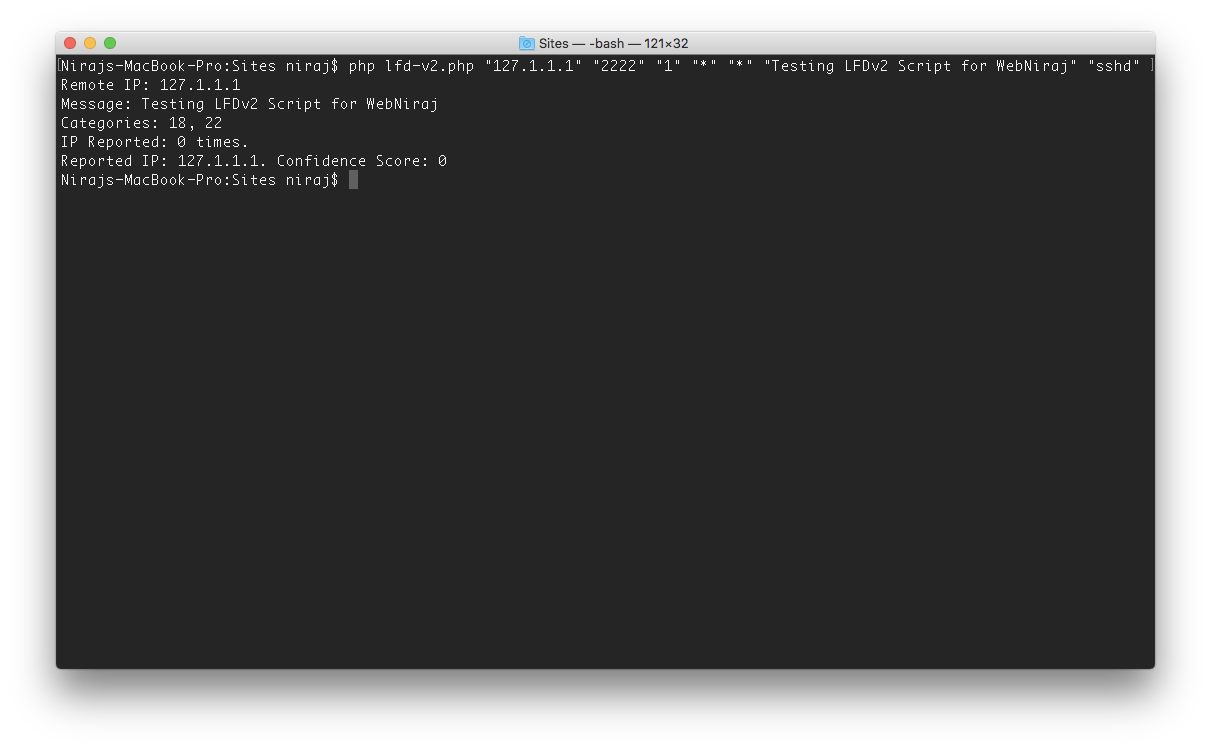
If the script reports the confidence score, the IP was correctly reported, and will therefore appear on the website:
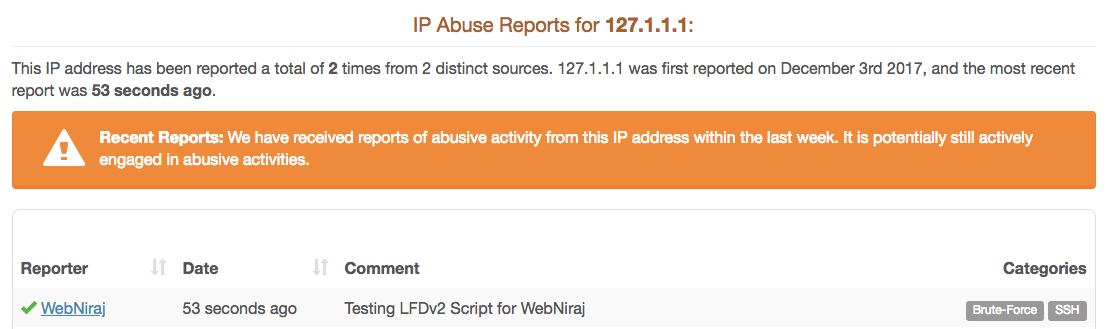

[…] UPDATE: This script has been updated to use v2 APIs. Please see the updated version here. […]
I can’t find /etc/csf/csf.conf file ? got latest directadmin running on CentOs
The
csf.conffile comes with the ConfigServer Security & Firewall plugin. It would need to be installed on your server before you can configure it.[…] a previous post, I’ve shared a script that allows server administrators to report abusive IPs to the Abuse IP database. But did you know […]
Good but some improvements mentioned here https://gist.github.com/niraj-shah/5395c080d28b02302ed6ea93bf9107ec#file-lfd-v2-php
@Clapper
Setup a snippet based off this version with your suggestions and some of my mods along with easy to implement usage for setting up on multiple servers.
https://gitlab.com/snippets/1981817
This is good, thanks @niraj-shah
How could we implement better privacy and redact the hostname that sometimes gets shown in the abuseipdb reports?
For example:
61.72.22.177 (KR/South Korea/-), 10 distributed smtpauth attacks on account [mailer-daemon@theuserdomain.net] in the last 3600 secs;
Would be good if we can show [redacted] or something?
61.72.22.177 (KR/South Korea/-), 10 distributed smtpauth attacks on account [redacted] in the last 3600 secs;
Suggestion – see this
https://github.com/centminmod/centminmod-abuseipdb-reporter/blob/master/abuseipdb-reporter.py
I’ve actually done something similar in the version that runs on my own severs. I have an array of terms that I want to hide, e.g. (add after line 27):
$hide = [ 'x.x.x.x', 'y.y.y.y', 'username1', 'username2', 'username3' ];Then on line 37, I added the following to find/replace the items I want to using a loop:
Thanks @niraj
I think it would be better to simply redact everything contained within the square brackets that LFD produces? How could we do that?
I will try your great suggestion meanwhile 🙂 Where is your “buymeacoffee” link? eh?
Cheers mate!
You could try a regex replace to find anything in the square brackets and replace it with REDACTED. A basic example:
preg_replace('/(.*)(\[.*\]+)(.*)/', '$1 [REDACTED] $3', $input_lines);See live example here: https://www.phpliveregex.com/p/LDN#tab-preg-replace