If you have a website or work with websites secured with OpenSSL, the heartbleed bug is something that will affect you. Heartbleed is a security bug in the open-source OpenSSL cryptography library, widely used to implement the Internet’s Transport Layer Security (TLS) protocol. While a fix for the bug was released on April 7, 2014, websites will be vulnerable until the servers have been patched.
Understanding the Heartbleed Bug:
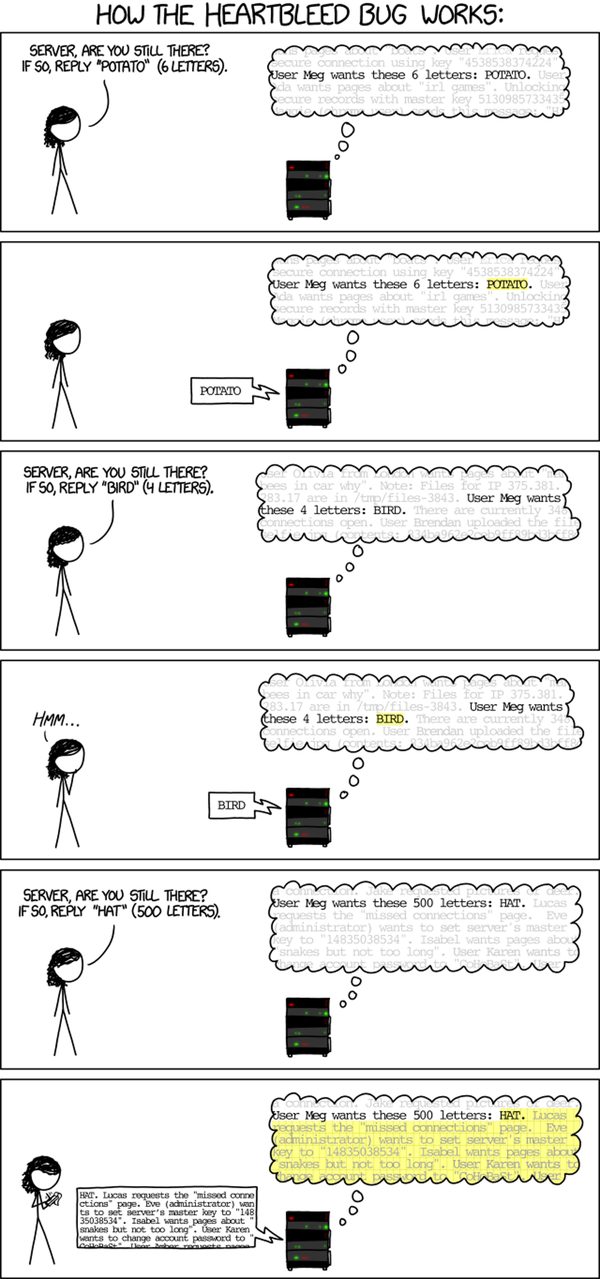
xkcd explains the heartbleed bug in a easy-to-understand comic:
Are you affected?
The best way to see if your website, or a site you use, is affected is by testing it for the Heartbleed bug. The tool, built by Filippo Valsorda, replicates the process in the comic above to obtain information from the server’s memory, often revealing information like passwords, credit card information and more.
How to Patch It
If you are using shared hosting space, it’s likely that your site has been patched already. If your site is showing up as VULNERABLE on the test site, you should contact your provider immediately to get the issue resolved. If you are a sysadmin, you can patch the system yourself using your repo management tool:
Redhat / CentOS:
yum update
Ubuntu:apt-get update
If you are unsure on how to patch your server, contact your provider or check their support site.
Once the patch has been installed, either reboot your system or restart any services that use OpenSSL, including Apache, MySQL, Email daemons, FTP servers etc.

[…] Qualys’ SSL Test is similar to ImmuniWeb’s one above. In addition to check various configuration issues, this report also tells you which browsers or devices your website may not work with. It also check is your server is vulnerable to various critical vulnerabilities like POODLE, and Heartbleed. […]